 |
| Image courtesy https://blogs.msdn.microsoft.com/commandline/ |
Display Wireless network password in clear text
netsh wlan show profile name=MyWiFiNetwork key=clear
The key=clear parameter gives us an ability to extract a WiFi password from any WiFi network (profile) stored on your computer.
Extract a list of Domain Admin users in the organisation
net group "Domain Admins" /Domain
By default the "Authenticated Users" group has Read access - any authenticated user in the organisation can execute this command to identify which users belong to which group. In the example about I used the Domains Admins group. This type of information is useful for the attackers - it gives them the "juicy targets" - which users to target (phishing, brute forcing etc) to get the domain admin privileges.
Get a list of all users in the domain
net user /Domain
Gives you a long list of all user accounts in the domains. Again, might be useful for the attackers - gives them another piece of a puzzle.
Get computer's IP address
ipconfig|find "IPv4"
This can be done in multiple different ways. Here I wanted to demonstrate the "piping" trick, where a vertical pipe character is used to combine 2 commands. And the trick is that the (standard) output of the first command is used ("piped into") by the second command. In our case the "ipconfig" command displays a lot of information but we use the "find" command to only display lines containing the "IPv4" - this gives us an IP v4 address of the computer.
In addition we can use another trick and push this information straight into the clipboard by piping the output of the "find" command into "clip"
ipconfig|find "IPv4"|clip
Display useful Wireless Network Connection information (WLAN)
netsh wlan show interfaces
netsh is a VERY powerful and useful command. Here we are using it to display information about all existing wireless network interfaces on our computer. This information is very handy when troubleshooting various network related issues.
We can also extract information about the wired interfaces - just replace "wlan" with "lan" in the command: netsh lan show interfaces
Display WiFi SSID
netsh wlan show interfaces|findstr "[^B]SSID"
It's great when commands like the one above dump a lot of useful information. But sometimes you just need this one piece - especially if you are running a batch file and want to identify a specific value. The previous example shows lots of different things including the SSID (wireless network name). If we just need to extract the SSID we can pipe the output into the "findstr" command. I decided to use "findstr" instead of a simpler "find" because it supports regular expressions. The first command displays both SSID and BSSID and I wanted to remove BSSID from the final result.
Get a MAC address
The netsh command that we used above to show interfaces' info can also be used to get the MAC addresses for each interface (disguised as a "Physical Address" in the output). But there is also a simpler command to do this:
getmac
It will display MAC addresses of all network interfaces that are present in the system.
Display system information
The "systeminfo" command contains tons of useful operating system configuration details. Run it without specifying any parameters first to see the variety of data it can provide you. Sometimes it might be beneficial to store all of that information in a file (e.g. to be imported into the centralised repository later on). For that purpose I would recommend changing the output to the CSV format. This will make import much easier:
systeminfo /FO CSV > c:\temp\sysinfo.csv
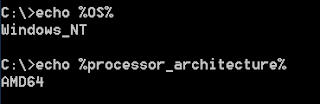
Using environment variables
Environment variables have been around since the MS DOS days. Just run the SET command to display them all in the console window. Each environment variable can be referenced by its name surrounded by the percent symbols.
See how each variable can be referenced in any other command:
echo %OS%
echo %PROCESSOR_ARCHITECTURE%
My only advice is try using environment variables everywhere you can instead of hard-coding certain values in your scripts.
Energy report (Officially: Power Efficiency Diagnostics Report)
powercfg energy -output c:\temp\energy-report.html
This is probably one of a less known commands. If you have never seen a report produced by this command - give it a go a see what kind of information it can give you. It is incredibly useful for troubleshooting any power, sleep, hibernation related issues.
On-Screen Keyboard
osk
As simple as that. It will bring a virtual keyboard on the screen - just in case you want to type with your mouse ;)
Bring up a User Accounts dialog
control userpasswords2
The new user accounts dialog window looks too fancy and less convenient to me (btw, you can access it via "control userpasswords"). But if you prefer the old style dialog then it's still there. You can bring it up by running "control userpasswords2" - even on Windows 10.
User, Group and Privileges Information
whoami /all
Without the "/all" switch whomai just returns the current logged in user name. With the addition of the "/all" switch you can see a lot more useful information including all groups this account is the member of (including UUIDs) and all privileges assigned to this account (things like SeIncreaseQuotaPrivilege, SeSystemtimePrivilege etc)
WMI
Now let's explore the power of WMI. WMI is an incredibly powerful way of interrogating various system parameters. I want to share a few useful examples with you just to demonstrate what's possible. We will use the wmic utility that comes standard on every version of Windows that was released after Windows XP.
Get motherboard manufacturer
We will extract this information from the win32_baseboard WMI class. To make it more interesting I will add a few additional command line techniques that you might find useful:for /f "tokens=9 delims= " %F in ('wmic baseboard^|more +1') do @echo %~F
Here we are extracting the 9th token (tokens in our case are space separated), which happens to be the motherboard manufacturer. Note: If a value contains spaces then they are treated as separate tokens by this method.
Using the FOR command to split a string into tokens is a generic way of handling strings from the command line.
I also wanted to demo the "more +n" trick. "more +1" means "skip the 1st line". The output consists of 2 rows - the table header and the row containing the actual values. We need this to skip the 1st (header) line in the output.
There is a more elegant way to extract values in wmic. And I will demonstrate it in the next example.
Get physical memory size
wmic computersystem get TotalPhysicalMemory | more +1
This gives us total physical memory installed in our system in bytes (we have 16GB in the example above).
We can also get max memory capacity (commit charge)
wmic memphysical get MaxCapacity | more +1
We see that we have roughly 32GB of RAM available - this includes the 16GB of physical RAM plus the size of the swap file.
Get a list of all applications that run automatically when a user logs into the system
wmic startup
Get version of the Adobe Acrobat Reader installed on your computer
wmic product get name,version | find "Adobe Acrobat Reader"
I hope you were able found a couple of useful commands. What are your favourite commands? Please share them in the comments section below.
Keywords: windows command line, command line tricks, useful commands, wmic, devops, sysadmin, systems engineering, microsoft windows







set devmgr_show_nonpresent_devices=1. and then devmgmt.msc. click on show hidden devices. Use this all the time in my retail POS stores to find out who is connecting their iPhones.
ReplyDeleteThat's good. I"m going to remember that one.
DeleteThis is also really great if uninstalling/reinstalling some device doesn't seem to be working. Only way to really get a clean install on the HP 8xxx series printers.
Deleterundll32.exe keymgr.dll,KRShowKeyMgr
ReplyDeleteShows an older version of the Credential Manager window. Useful if there is a corrupt set of credentials being stored in credential manager, as the Win7 to Win10 normal version of Credential Manager may not display those corrupt credentials. Recently ran into this with a bunch of users that did XP to Win7 upgrades on PCs that came with the license.
Thanks for this
ReplyDeleteWMIC BIOS Get Serialnumber, for serial number o your machine.
ReplyDeleteFor Dell/HP etc vendors.